Uncover Vulnerabilities Before They Become Risks
Comprehensive suite of automated security scans across IP, domain, and web application layers.
Uncover Hidden Vulnerabilities
We use 150+ tools under the hood to detect and fix security flaws before they become a costly breach.
Prevent Potential Losses
Proactively safeguard your business, protecting valuable data and reducing downtime.
Save Time & Money
Automated scans provide immediate insights, helping you avoid expensive incident response and legal fees.
Automated Security
Comprehensive suite of automated security scans across IP, domain, and web application layers.
Analyze your external surface frequently to make you aware of what is exposed.
Single IP or IP ranges
- TCP Scan Discover open TCP ports and check for vulnerabilities
- Discover open UDP ports and potential issues
- IP Reverse Lookup
- Resolves an IP to its associated domains using reverse DNS
- Queries the 3rd party APIs to find all domains associated with an IP address — uncovering linked infrastructure
- IP Blacklist status
- CouchDB, ElasticSearch, FTP, MongoDB, MySQL, PostgreSQL, Redis, SMB, SSH, and more — using customized wordlists
- many more...
Automated discovery of misconfigurations and vulnerabilities in your environment.
Domains or subdomains
- Detects suspicious domain variations resembling the legitimate domain — flags potential phishing risks
- Resolves DNS records, WHOIS data, checks for takeover risks, and extracts metadata (titles, redirects)
- Queries 3rd party sources to check for breached data linked to the domain
- Uses tools for fast, passive subdomain discovery, discover subdomains from multiple public sources
- Checks if PTR records expose internal/private IPs.
- Analyzes mail security settings to identify spoofing/phishing risks
- Finds dangling/unclaimed subdomains vulnerable to takeover
- Collects emails from public sources — validates and filters results
- Tests nameservers for misconfigurations exposing full DNS zone data
- Email leaks, blacklists, and related organization info
- Google Dorks search via CSE
- many more...
Detection of various web vulnerabilities.
Web URLs / websites
- Finds server version + framework version
- Tests inputs for OS command injection vulnerabilities
- Tests inputs for sq/ noSql injection
- Attempts to read sensitive files by injecting crafted paths
- Identifies unvalidated redirect parameters leading to attacker-controlled destinations
- Detects template injection vulnerabilities that may allow code execution
- Tests if redirect parameters allow obfuscated javascript payloads — combining XSS & open redirect
- Automated OWASP Top 10 (SQLi, XSS, etc.)
- SSL/TLS misconfigurations & certificate issues
- HTTP header misconfigurations
- Backup file detection
- Authentication bypass
- Login & weak password brute-force (if configured)
- Various other misconfigurations discovery
Request initial scan for your domain for free
Keep your security up-to-date.
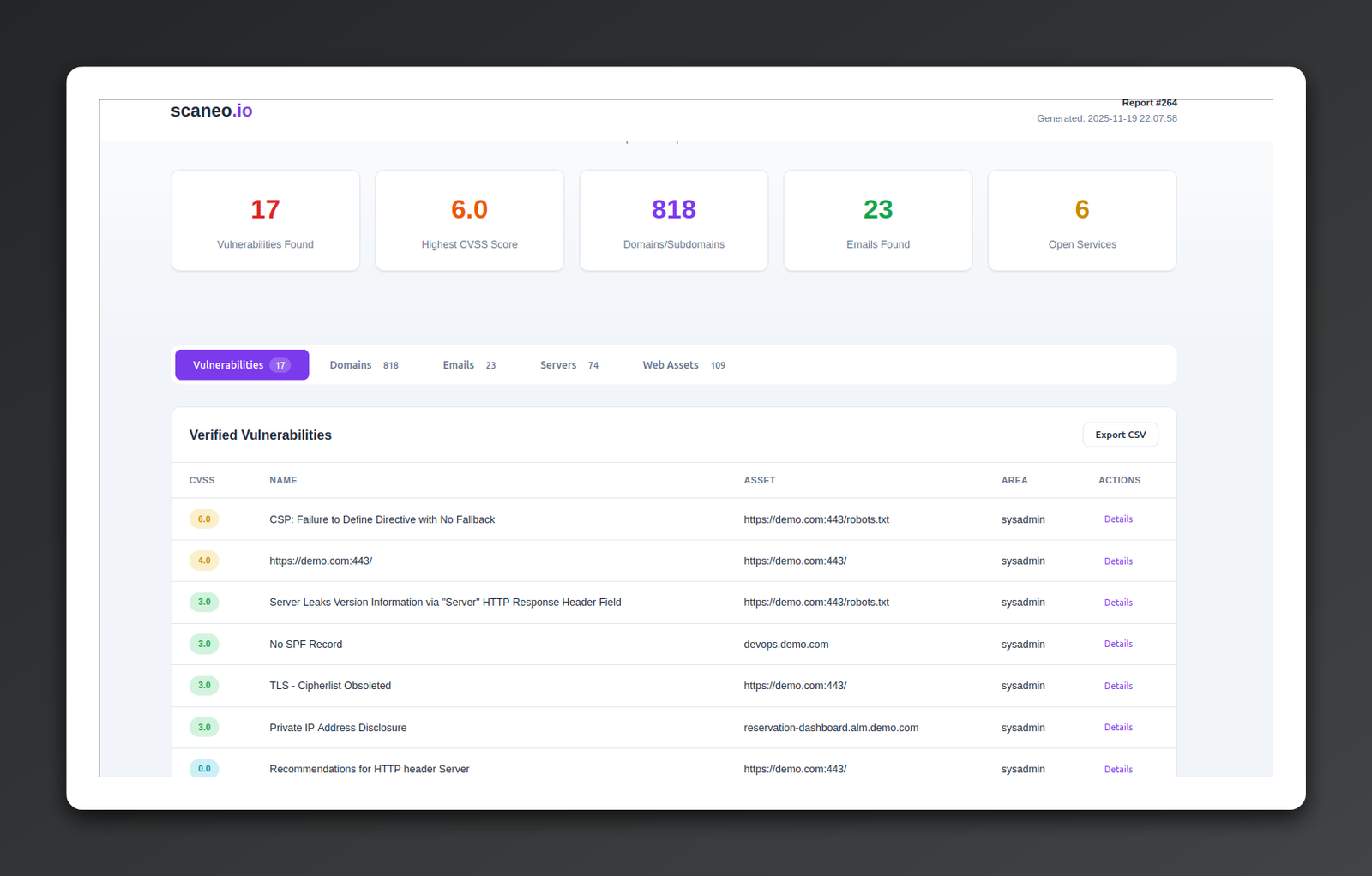
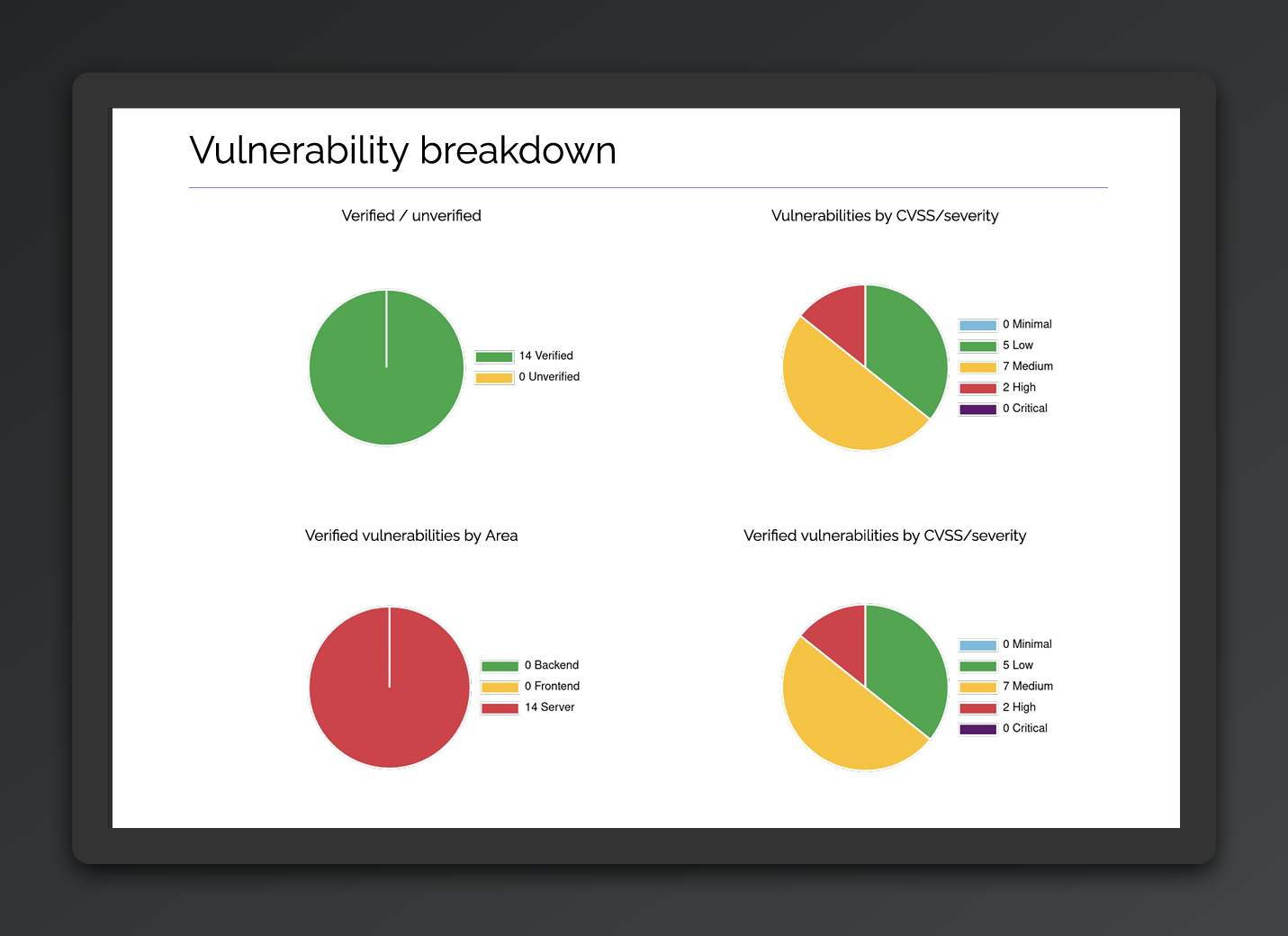
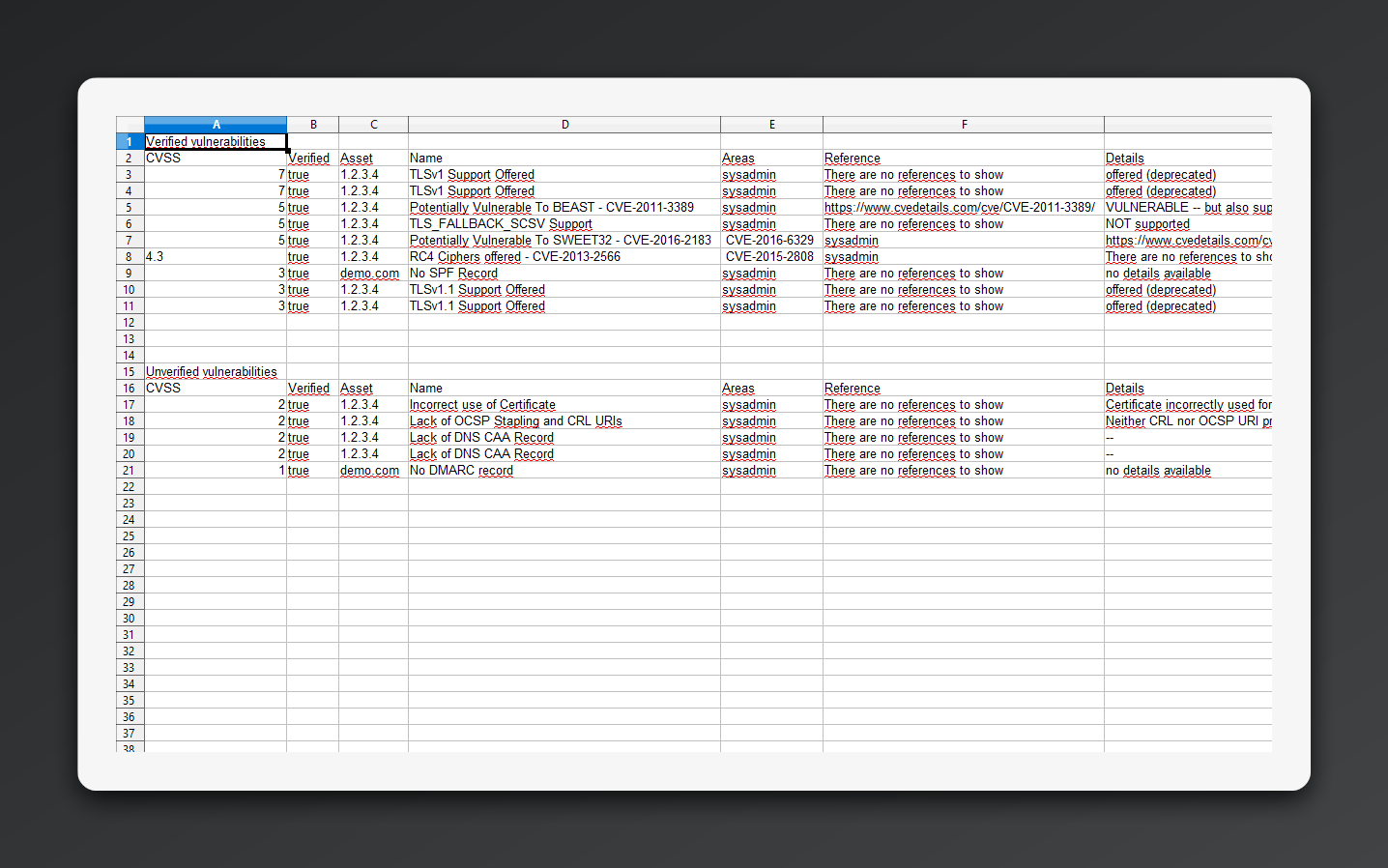
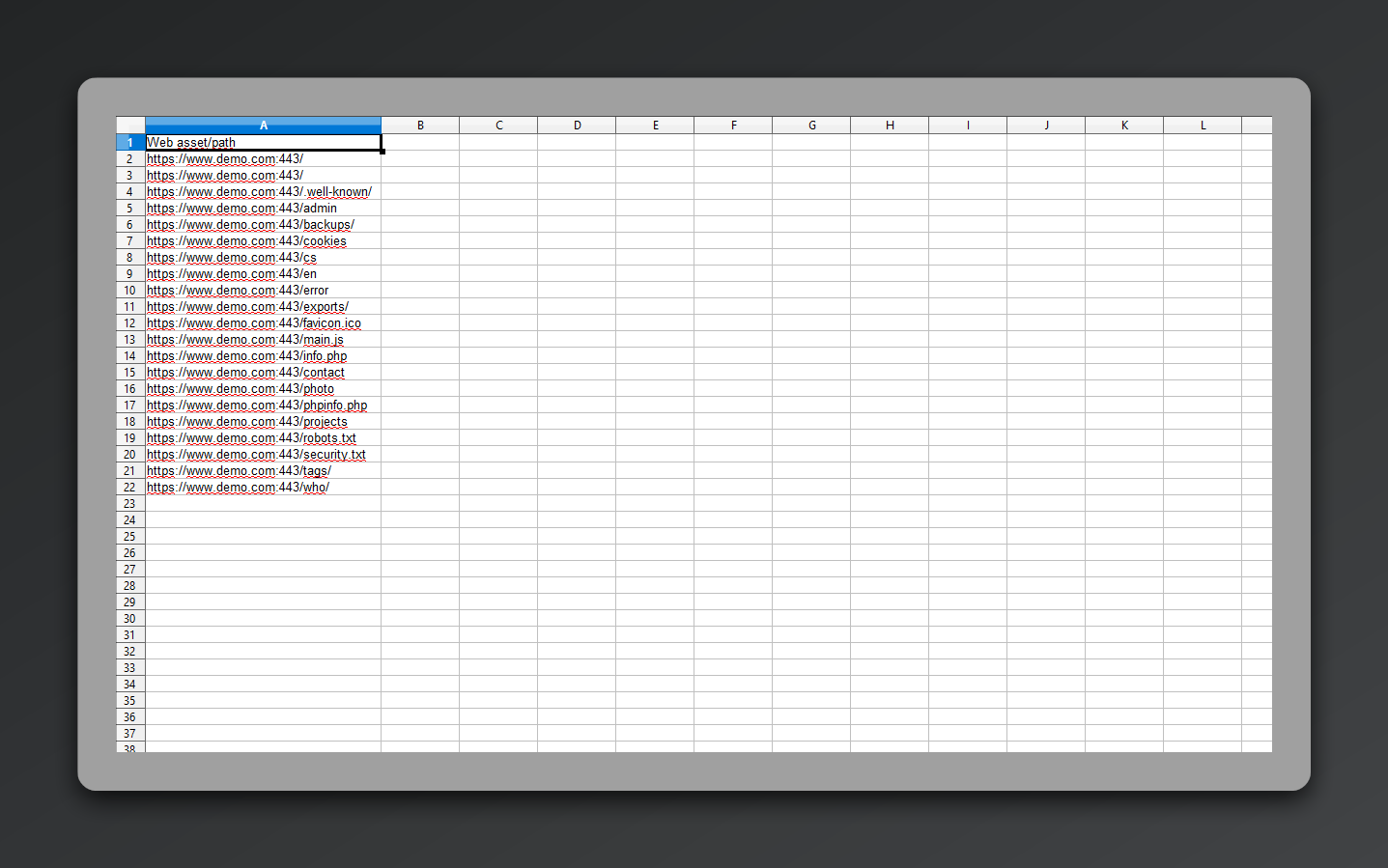
Example Security Reports
See what you'll receive - comprehensive security analysis with detailed findings
Trusted by Security-Conscious Teams
Protecting businesses across industries